Disclaimer
This blog post is a part of NSA Codebreaker 2024 writeup.
The challenge content is a PURELY FICTIONAL SCENARIO created by the NSA for EDUCATIONAL PURPOSES only. The mention and use of any actual products, tools, and techniques are similarly contrived for the sake of the challenge alone, and do not represent the intent of any company, product owner, or standards body.
Any similarities to real persons, entities, or events is coincidental.
Synopsis
Aaliyah is showing you how Intelligence Analysts work. She pulls up a piece of intelligence she thought was interesting. It shows that APTs are interested in acquiring hardware tokens used for accessing DIB networks. Those are generally controlled items, how could the APT get a hold of one of those?
DoD sometimes sends copies of procurement records for controlled items to the NSA for analysis. Aaliyah pulls up the records but realizes it’s in a file format she’s not familiar with. Can you help her look for anything suspicious?
If DIB companies are being actively targeted by an adversary the NSA needs to know about it so they can help mitigate the threat.
Help Aaliyah determine the outlying activity in the dataset given
Downloads
DoD procurement records (shipping.db)
Prompt
Provide the order id associated with the order most likely to be fraudulent.
Solution
Upon inspecting the file, it ends with .db file and doesn’t really much make sense.
So what I did was to check the correct mimetype so I can properly determine the right tool for it.
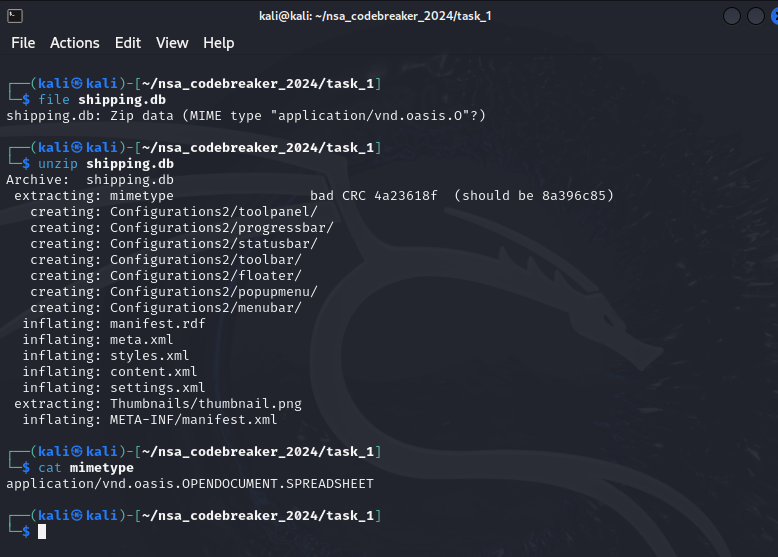
Upon checking some documentation and other references, I think it is an .ods file.
References:
https://stackoverflow.com/questions/31489757/what-is-correct-mimetype-with-apache-openoffice-files-like-odt-ods-odp
https://www.iana.org/assignments/media-types/application/vnd.oasis.opendocument.spreadsheet
Upon opening it with spreadsheet, we are greeted by gigantic dataset.
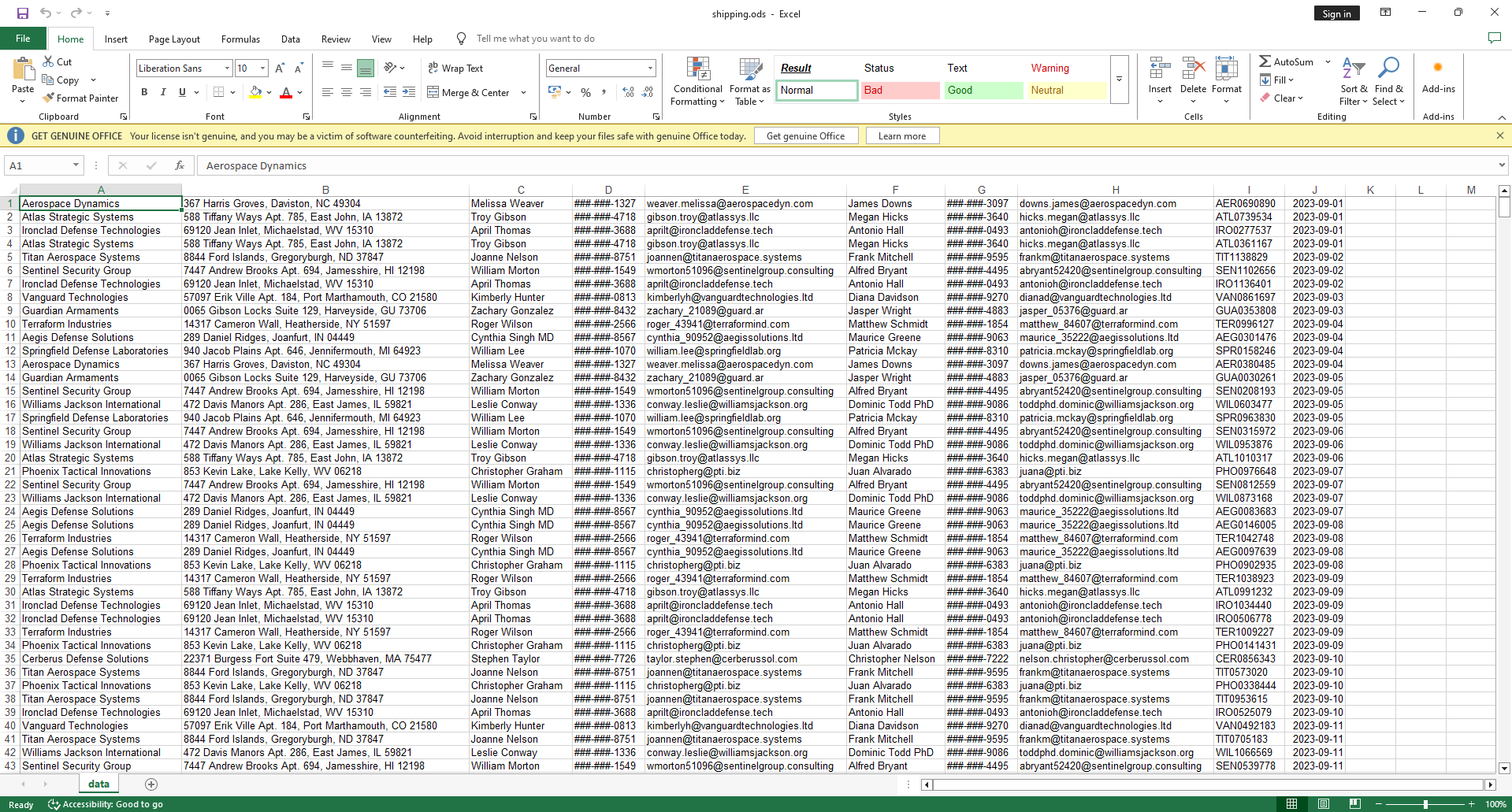
Our goal is to find something suspicious, so I tried to arrange them to find an outlier in the dataset.
So what I did was to arrange them accordingly and manually checked for outlier. And there we go! We spotted it.
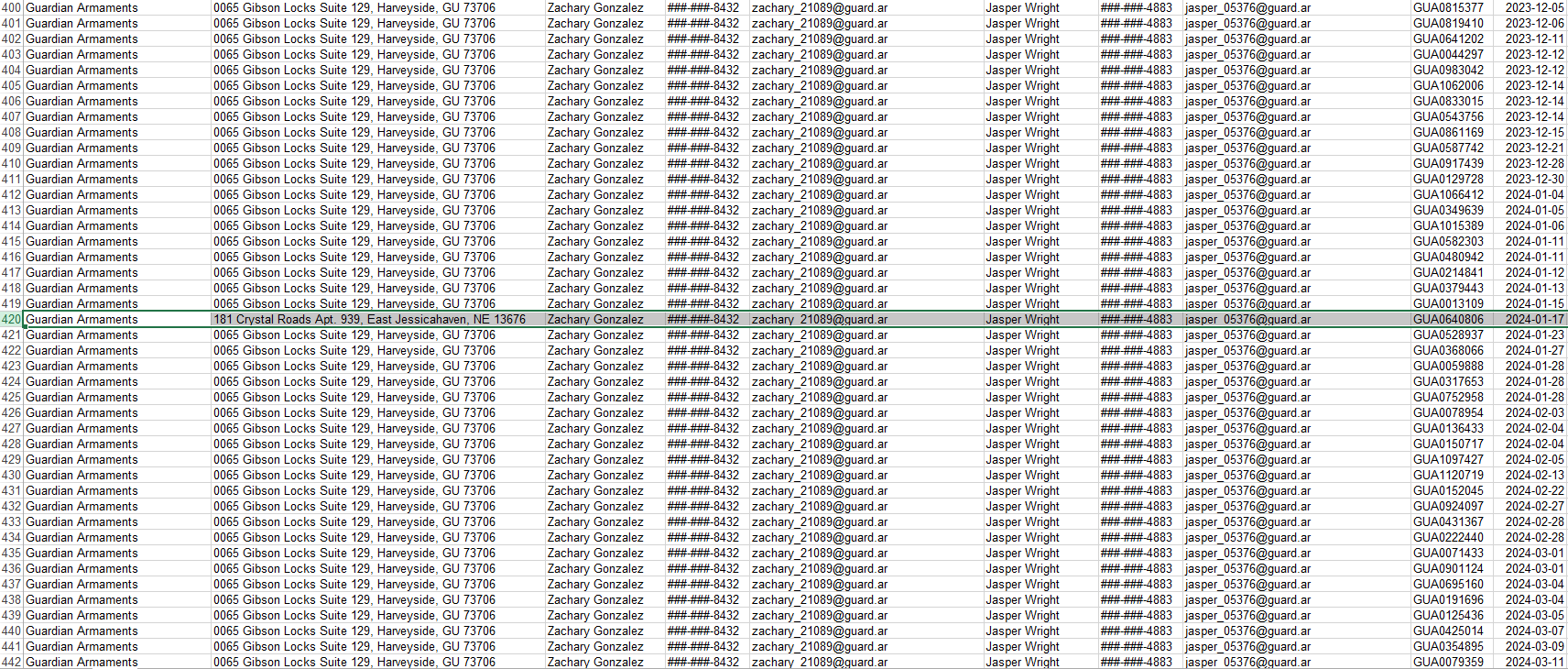
I submitted the order id and viola! Task 1 is done!
Remember this information as we will be needing this in the later task: jasper_05376